Today, there are many wireless security standards available on the market. Which one uses a 128-bit key?
Wireless networks, although purposeful, can also be dangerous. Four different WiFi security protocols protect data trading. Each uses a standard Bit Key number that enhances protection against hackers or malicious software.
Wired Equivalent Protection (WEP), WiFi Protected Access 2 (WPA2), and WiFi Protected Access 3 (WPA3) use 128-bit keys. Even though they use the same amount of bits, they offer different protection levels.
I’ll go into more detail below.
What is a Wireless Security Standard?
Wireless Security Standards are protocols that encrypt information in wireless networks.
The WiFi Alliance created them. Their role is to keep all data hidden and secure wireless connections. They protect any communication that happens in such channel systems. Their purpose is to create powerful and impenetrable barriers against hackers.
Their operation method includes encrypting data transfer using a specific number of bits. That happens by using cryptographic keys to randomized data.
Wireless Security Standard includes:
- Wired Equivalent Protection (WEP)
- WiFi Protection Access (WPA)
- WiFi Protection Access 2 (WPA2)
- WiFi Protection Access 3 (WPA3)
The first three (WEP, WPA, and WPA2) use symmetrical encryption, while WPA3 uses a different, more advanced authentication method.
Symmetrical encryption uses the same key to encrypt or decrypt data, while WPA3 generates new keys for every data unit.
They are crucial for data protection since wireless networks are far less secure than wired ones.
What is WEP?

WEP is Wired Equivalent Protection.
It was established as a security standard in the year 1999. It is the oldest one created and thus vulnerable to breaches due to technological advancements.
WiFi security uses encrypting with 64-bit and 128-bit keys.
It was taken down in 2004.
What is WPA?

WiFi Access Protection is the descendant of WEP.
It was released in 2003. This WiFi security protocol was created by the WiFi Alliance to address the issues of WEP.
It uses 256-bit keys and the TKIP (Temporal Key Integrity Protocol). TKIP creates new bits for every package or unit of data.
It is more potent than WEP but inefficient for the technology used nowadays.
What is WPA2?

WiFi Protection Access 2 is WPA-updated hardware.
Their main attribute is the Advanced Encryption Standard – AES Block Cipher function. The key size can be 128-bit, 192-bit, or 256-bit. No matter the size of the key, the encryption is executed in 128-bit blocks.
The AES Encryption Algorithm enhances the authentication and encryption of data. That is why WiFi Protected Access 2 is the second-best security protocol.
The AES Block Cipher function replaces the Temporal Key Integrity Protocol.
What is WPA3?

WiFi Protected Access 3 is the final and most optimal security protocol.
It does not use the Advanced Encryption Standard.
It uses Simultaneous Authentication of Equals (SAE), which is a new type of authentication method. Its primary role is to minimize password cracking. SAE provides a unique key to each WiFi authentication.
WPA3 has two modes:
- Personal
- Enterprise
Both use the SAE.
WPA3 Personal allows more optimal authentication based on not necessarily complex passwords. It uses a 128-bit key.
WPA3 Enterprise is to replace WPA2 in the longterm. It utilizes 192-bit keys as opposed to WPA2 Personal.
Which of The Wireless Security Protocols Use 128-Bit Keys?
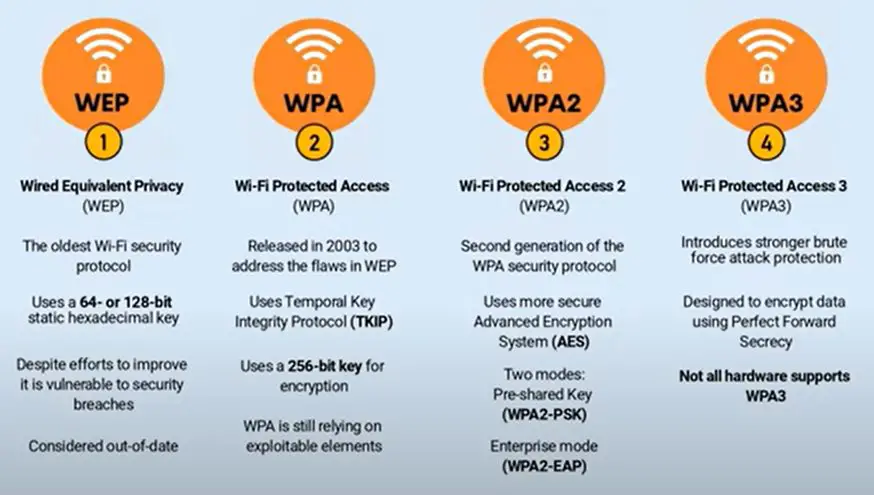
As shown above, out of the four protocols, only three use a 128-bit key.
- Wired Equivalent Protection
- WiFi Protection Access 2
- WiFi Protection Access 3
Although WiFi Protection Access uses a 256-bit key, WPA2 and WPA3 have additional encryption and authentication systems that protect data.
Wrapping Up
The WiFi alliance manages and certifies all protocols.
WEP, WPA2, and WPA3 use a 128-bit key (among other keys). WPA, which has been characterized as inefficient, uses a 256-bit key.
The four WiFi Security Standards offer different defense levels.
WEP is considered discontinued because hackers can easily penetrate it.
Take a look at some of our related articles below.
- How to use cellular data for security camera
- How to connect wireless mouse to chromebook
- What network does Cintex wireless use
Video References
BusinessTechWeekly
PowerCert Animated Videos